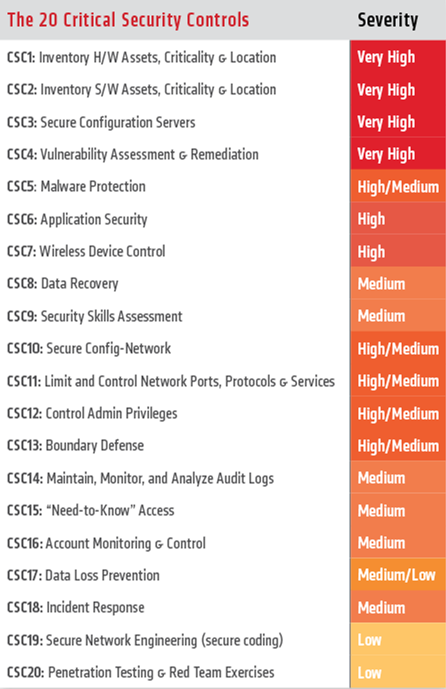
The Critical Security Controls: Basic Cybersecurity Hygiene for your Organization | Qualys Security Blog
Free Microsoft 365 Assessment Tool based on the top 20 Critical Security Controls from CIS and the Council on Cybersecurity | by Alex Fields | REgarding 365

The Critical Security Controls: Basic Cybersecurity Hygiene for your Organization | Qualys Security Blog

Twitter 上的Michael Fisher:"What are the top 20 controls for a healthy network #Security posture? {Infographic} #CyberSecurity #infosec #education #DevOps #Malware #databreach #Pentesting #IRP https://t.co/M6bSaA0361" / Twitter